Before starting this article, I want to have a big bold reminder for you. If you want to have any chance of an eventual end user hack, do not update your Switch past 2.0! If you are afraid that you may not be able to access the eShop of the Switch, think again. We have instructions for you to bypass the update process and go on the eShop.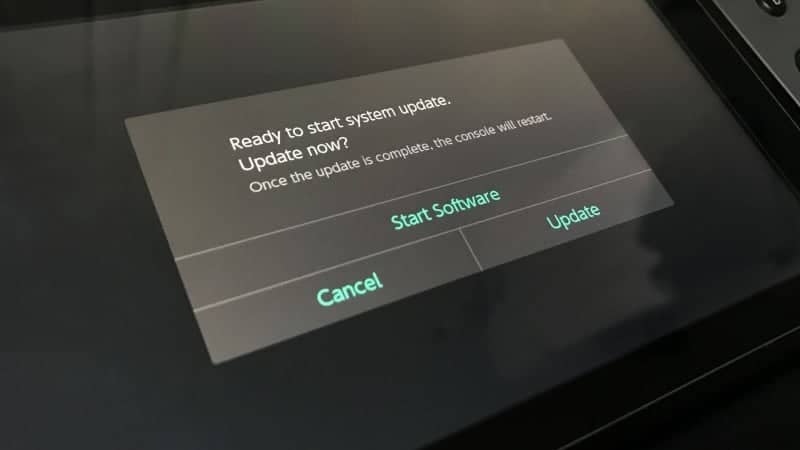
Okay, now onto the business at hand.
By now you should all know that the Switch was shipped out with a WebKit that had known vulnerabilities on it. It only took hackers days before they had access to more than we should have had. For example, there is no accessible web browser on it, but hackers found a way. And there was no streamable video in the web browser, but then hackers found a way. See Pegaswitch if you are interested in those hacks. After that first week, things seemed to have slowed down on the Switch hacking front. But apparently that wasn’t the case, hackers have been working hard at getting into the meat and potatoes of the Switch.
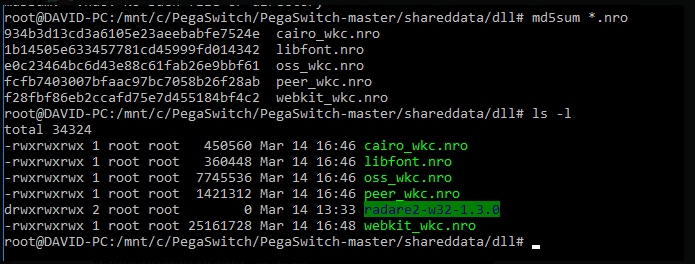
PegaSwitch v1.5-ish is out. Big changes: Significantly higher hit rate (99.75% within the first three tries, which are now automatic) meaning you should never have to restart your browser or device to get it to trigger The garbage collection beast has been slain, so you should no longer see crashes when doing big things, e.g. full memory dumps The entire exploit itself is now separated from sploitcore, so swapping this out for different Webkit exploits in the future is totally possible now, without breaking the API in any way
If you are familiar with Plutoo, hacker extraordinaire, of WiiU and 3DS fame, you’ll know that he is quick to hack and quick to share his progress and he is always one of the trustworthy ones in the scene. Apparently, he showed off (picture at the bottom) that he was able to pull API call names and other data from just one of the many modules on the Nintendo Switch. The module specifically called the NS, which he believes is indeed the same module that is titled NS on the 3DS. However, he has mentioned that even though there are a lot of similarities in the API call names within said module, that doesn’t mean that the Switch is running code based off of the 3DS.
Thus far, all that the exploit lets the hackers view are sections of the RAM and portions of the file system. The RAM that they’re able to view is the very same RAM that is accessible to the webkit. Within the RAM that is viewable, they’re able to view the modules that the webkit is able to use and that’s, at this point all that they have access to. But we’re talking about Plutoo here (and most likely others that are behind the scenes) and they will keep poking and probing until they find a useful hole within the modules and that will be what will finally be what gets them beyond the webkit modules and further into the system!
Stay tuned, we will keep bringing you updates as they come, here on Hackinformer.com and follow us on Twitter @Hackinformer
 Hackinformer Your device needs to transform, we are here to inform
Hackinformer Your device needs to transform, we are here to inform