Another promised Christmas gift is here! This Kernel Exploit release will make firmware 4.05 the new 1.76 and more people should finally be able to make use of some tools! Yay! But if you updated then its time to do a little pawn shopping, eBay, craigslist, etc.. to find the right PS4 & FW for you.
https://twitter.com/SpecterDev/status/945920806630014976
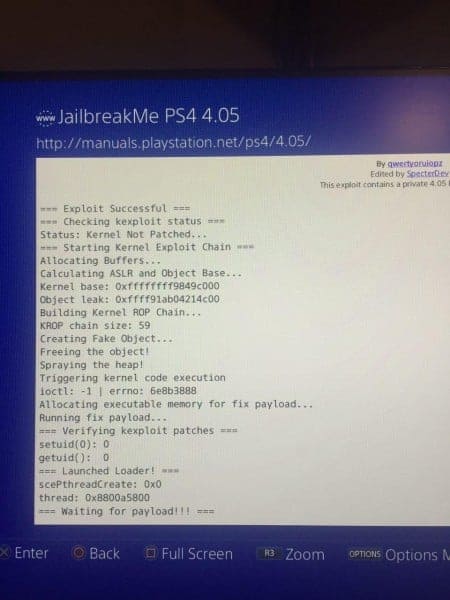
The kernel exploit itself is the very same exploit named “namedobj” which team fail0verflow talked about in detail a couple months ago! Finally, here we have the first full implementation of this exploit made user-friendly thanks to SpecterDev!
This release however, does not contain any code related to defeating anti-piracy mechanisms or running homebrew. This exploit does include a loader that listens for payloads on port 9020 and will execute them upon receival.
As you can see this is a very basic payload executer as of now and no CustomFirmware, user-friendly hack or whatever!! Just like with 1.76 there will be full kernel access and a lot of possibilities of course, BUT if you are looking for easy Homebrew launching and I$O loading, this release is still not for you. Go get a P$3..lol
As SpecterDev also notes; His implementation is very stable as well with a trigger success-rate of 95%!
https://twitter.com/SpecterDev/status/945875405466042368
How to download / install
First of all: You will of course need to run Firmware 4.05!
– If you are below that, here is a simple guide on how to manually upgrade your firmware.
– If you are above that number, sorry you are out of luck for now.. :/
Now, as its a so called JailbreakMe implementation everything works from the webbrowser. So what you would need to do is download the following files from SpecterDev’s Github, upload it to some sort of local server and navigate your webbrowser to it! From there the exploit will trigger by itself, all necessary patches will be applied automatically and the payload of your choice will be executed by your PS4 when you send it!
Here is an example payload by SpecterDev himself which will activate the DebugSettings for you to play with!
https://twitter.com/SpecterDev/status/945936137817694208
Credits & Thanks
I was not alone in this exploit’s development, and would like to thank those who helped me along the way below.
qwertyoruiopz
Flatz
CTurt
Anonymous
A technical write up should follow soon and the PS4 is wider open than ever before! Things should start moving again with more people having access now.
https://twitter.com/flat_z/status/945925011445108736
So lets see what ‘greatness awaits’ us now!
Thank you SpecterDev!
Downloads
Exploit files via github, Example Payload: DebugSettings
And to make your lives easier here is an online version so you won’t need to host the files yourself thanks to Darthsternie: darthsternie.bplaced.net/PS4Xploit/4.05/