After some anonymous source has released a dump of the NVidia Tegra 210 BootROM yesterday it seems that today the same source has released the BootROM exploit further known as Fusee Gelee. With the Bug used in Fusee Gelee now being open to the public KTemkin has released her write-up of the exploit involved with this and the Fusee Gelee Loader which allows loading Payloads.
As had already been mentioned before many times this Exploit is unpatchable by software means and can only be patched with a new hardware revision. The Exploit is tethered which means the Switch needs to be connected to a PC everytime the exploit should be run. The Exploit makes use of a flaw in the Tegra Safe Mode to execute payloads sent to the switch at boot time.
To be able to use this you currently need the following:
A PC running Linux (Live USB or normal Linux) with USB 3.0 (This MAY also work on Linux in a VM but I still have to get it running that way; Virtualbox needs the addon pack for this)
A Switch
Very probably a screwdriver to take apart your right joycon or at least something tiny to bend one of the pins
If you have all this then you can use Fusee Gelee right away but before you get all hyped up now about using Atmosphere CFW or something else I have to tell you that you can only run a test payload at the moment which displays your Switch ID and some other Stuff. If you still want to continue then here’s a simple write-up about what you need to do.
1. Install Python3 and pyusb on your Linux Machine (For Ubuntu that would be sudo apt-get install python3; sudo apt-get install python-pip and sudo pip install –pre pyusb)
2. Next up download the Fusee Gelee Launcher and the POC Payload
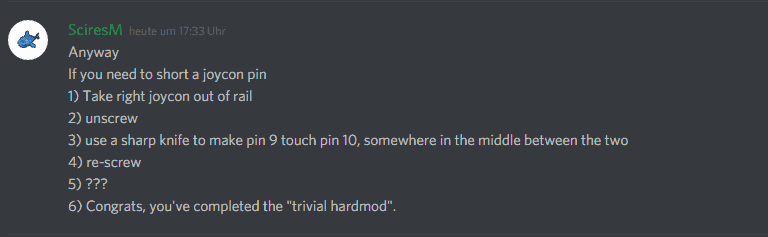
3. Now take your Right Joycon (It needs to be the right one and not the left one) and either screw it apart which I recommend or try to CAREFULLY bend the two following Pins in your Joycon:
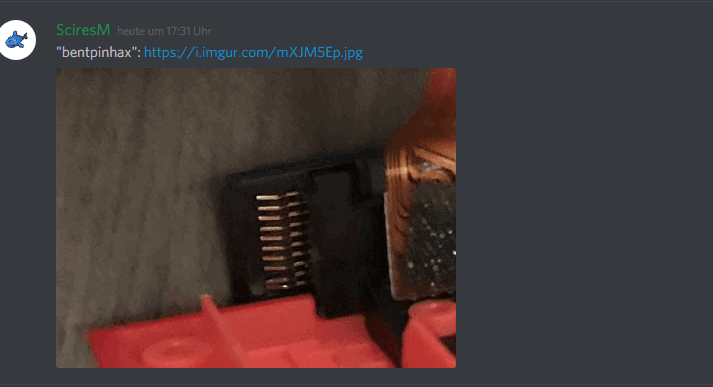
4. If you’ve done that just put the Joycon back together and onto your Switch again. Power off your switch now if it isn’t powered off yet. This bent pin does not affect the usability of the joycon in any way so you can just leave it like that forever. Think of it like a PSP Pandora Battery but for the Switch ^^
5. Extract the Fusee Gelee Launcher and copy the fusee.bin file into the root of the folder so that it looks like this:

6. Now for the final Step connect your Switch to your PC with a USB A to USB C Cable and power it on while holding VOLUME_UP. If all went well your Switch should be stuck on a black screen. If it boots into the normal OS I suggest taking another look at the Pins you bent.
Lastly, execute the fusee-launcher.py file by opening a terminal window in the folder and writing “sudo python3 fusee-launcher.py fusee.bin”
Congrats your Switch should now greet you with a nice little info Screen with some important information about your Switch. That said you shouldn’t run around posting pictures of your Switch’s Private Keys all over the Internet.
If you are interested in a write-up as to how this exploit works KTemkin did a wonderful write-up explaining exactly how all of this works. You can find the write-up here.