I know you must be anxious to read this. We’ll cover everything that has been announced so far and what it means for the future of the PS4. If you’ve been saving a PS4 higher than 5.05 for a newer kernel exploit, you may just be getting what you’ve been dreaming of. Let’s just dive right in.
The announcement came by way of a tweet from TheFloW directly:
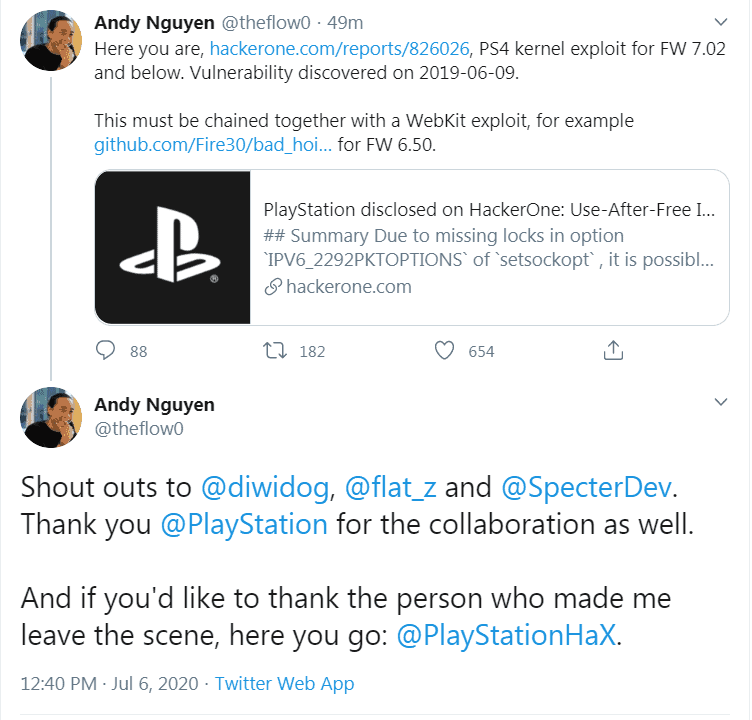 The Breakdown: via hackerone.com
The Breakdown: via hackerone.com
“Due to missing locks in option IPV6_2292PKTOPTIONS of setsockopt , it is possible to race and free the struct ip6_pktopts buffer, while it is being handled by ip6_setpktopt. This structure contains pointers (ip6po_pktinfo) that can be hijacked to obtain arbitrary kernel R/W primitives. As a consequence, it is easy to have kernel code execution. This vulnerability is reachable from WebKit sandbox and is available in the latest FW, which is 7.02.”
Attachment: Attached is a Proof-Of-Concept that achieves a Local Privilege Escalation on FreeBSD 9 and FreeBSD 12.
Impact: In conjunction with a WebKit exploit, a fully chained remote attack can be achieved. It is possible to steal/manipulate user data, plus dump and run pirated games.’
The Future:
Right now, the only WebKit in existence is one that is for PS4 firmware 6.72. As of now, it’s been added to 6.72 Mira for all PS4’s on that firmware.
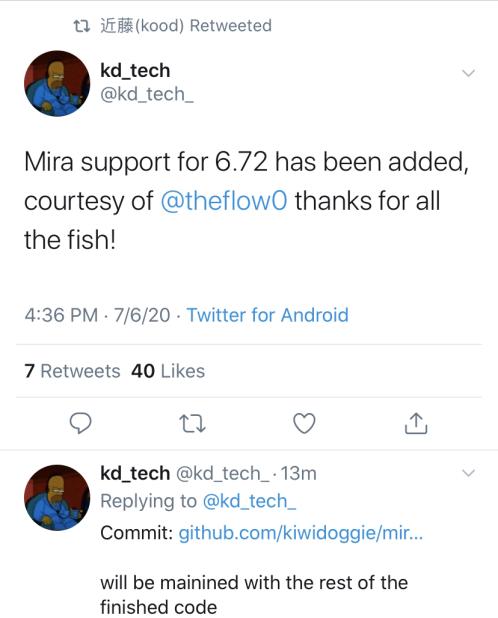
If you’re not sure, you should be able to update to 6.72 and use Mira with no problems. We’ll post instructions for those new to Mira very soon. If you’re between 6.72 and 7.02, wait patiently. We’re waiting on a WebKit exploit and then you’ll have access to what the rest of us have. Do not update out of frustration and be aware that there is no way to downgrade.
