I’m here today to bring something to everyone’s attention and it’s something I think everyone should be aware of. The first one is ransomware-type virus called GoldenEye and the other is a helpful guide to help you to stay safe.
What is ransomware? “It’s a type of malicious software designed to block access to a computer system until a sum of money is paid.
MISCHA and Petya differ in that MISCHA only encrypts certain files, while Petya encrypts the hard drive itself (thus, making it impossible to use the computer properly). GoldenEye, however, performs both of these tasks. Petya ransomware was designed to infiltrate the system and attempts to overwrite the system’s MBR (Master Boot Record). To achieve this, Petya must obtain administrative permissions. If the user denies these permissions, the encryption process simply stopped. If, however, the permissions are given, Petya modifies the MBR with a custom boot loader.
Petya automatically reboots the computer, displays a fake check disk (CHKDSK) screen and encrypts the hard drive in the background. It then displays a ransom demand message using ASCII Text Art. The message is temporarily displayed when booting the computer. MISCHA, on the other hand, does not attempt to modify the MBR – it simply encrypts files.
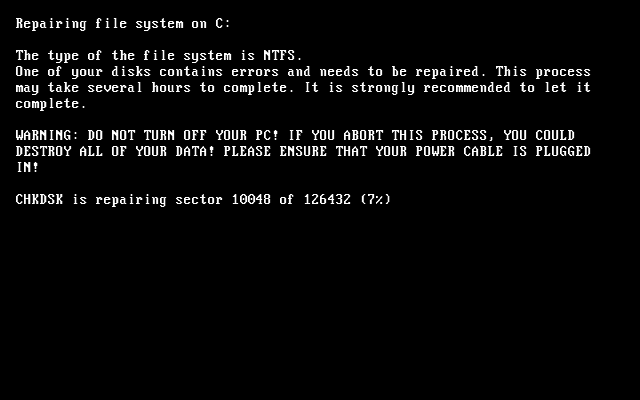 This behavior is very common to regular ransomware-type viruses. GoldenEye performs these actions in reverse: it encrypts data and only then attempts to modify the MBR, thereby preventing victims from stopping the encryption process (by denying permissions).
This behavior is very common to regular ransomware-type viruses. GoldenEye performs these actions in reverse: it encrypts data and only then attempts to modify the MBR, thereby preventing victims from stopping the encryption process (by denying permissions).
In addition, GoldenEye creates a text file (“YOUR_FILES_ARE_ENCRYPTED.txt“, containing an identical message) and places it in certain folders (e.g., Desktop, My Documents, etc.) Furthermore, GoldenEye appends eight random characters to the name of each encrypted file (e.g., “sample.jpg” might be renamed to “sample.jpg.g8k3jmol“).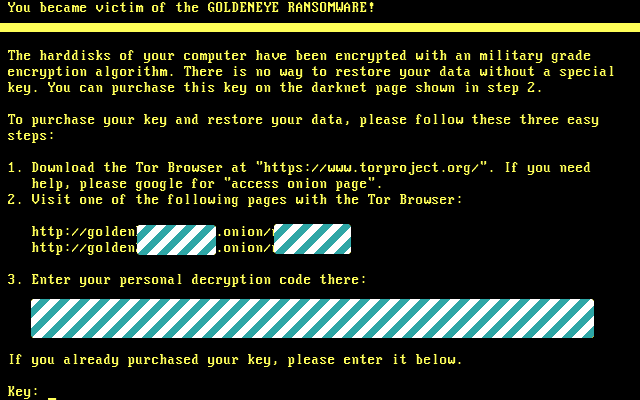
Now that’s not all it also demands a ransom payment of 1.31034193 Bitcoins (approximately $1000) for decryption. To submit pay, victims must follow instructions provided on GoldenEye’s Tor website (the link is provided within the ransom-demand message). Note: paying does not guarantee that your files will ever be decrypted. And just so you know most if any will ever return control or unencrypt your files so paying just lines there pockets and rips you off as well.
So you may be asking what can I do? Here are a few steps that can help keep you safe.
- Don’t store important data only on your PC.
- Have 2 backups of your data on an external hard drive and in the cloud – Dropbox/Google Drive/etc.
- Make sure Dropbox/Google Drive/OneDrive/etc. application on your computer is not turned on by default. Only open them once a day, to sync data, and close them once this is done.
- Your operating system and the software you use is up to date, including the latest security updates.
- For daily use, don’t use an administrator account on your computer. I use a guest account with limited privileges. This may not always be easy to do but worth it for safety sake.
- Adjust your browsers’ security and privacy settings for increased protection.
- Remove outdated plugins and add-ons from your browsers. Only keep the ones you use on a daily basis and keep them updated to the latest version.
- Use an ad blocker to avoid the threat of potentially malicious ads.
- Never open spam emails or emails from unknown senders, never download attachments from spam emails or suspicious emails, and never click links in spam emails or suspicious emails.
- Use a reliable, paid antivirus product that includes an automatic update module and a real-time scanner.
Now this is just some of what you can do to keep you safe you can also look HERE for a helpful guide by Sophos for dealing with GoldenEye and other ransomware.
You can also try HERE if you have been infected by GoldenEye
So please keep yourself safe, be careful of what you open in emails, and keep your security and antivirus up to date. Your best bet is to keep your eyes open to fishy looking links and emails while online.
Thank you for reading and keep doing it for the love of the game.