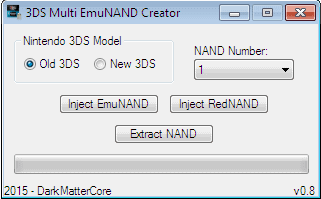
User DarkMatterCore has been working on a very interesting project. He has discovered that you are able to write up to 4 different emuNANDs on one single SD card. His project has matured to the point of having a decent GUI and is very user friendly.
The program is compatible with the O3DS and N3DS models with every region. With this program it’s possible to have emuNAND and CFW on the same SD. This is only recommended for advanced FW4.X users and typical users can still enjoy the basic features. If you have the knowledge and wish to use a CFW one can be setup and downloaded here.
NEVER and I mean NEVER install CIA files to the sysNAND, without having access to a NAND MOD. A modification like this should only be done by a professional and even then you need to understand how to backup and restore your NAND from a computer.
I have never installed to the sysNAND and never will! The 3DS scene has not provided a custom recovery and that’s one of the reasons why gateway’s emuNAND is so popular and safe. Do not risk your investment or lose your opportunity with the 3DS scene! In the end, applications like FBI and Pasta CFW are not worth it!!!!!
Make sure before running the program, that it has administrative privileges. This program detects all drives to locate the source with EmuNand automatically, making the process straight forward. You won’t be able to inject RedNAND into N3DS, as Palentine’s CFW is not compatiable. It reads/writes the NAND dump and make sure to backup the data present in the FAT32 partition. I’m sure in time many 3DS devs will utilize this tool and make more options for the N3DS users. An example of redNAND can be seen below.
Multi EmuNand Changelog:
VERSION 0.8
- Program ported to Win32 API, so now it finally has a proper GUI. It still is written in C and compiled with MinGW. Props to my good ol’ friend Xiangua/Nana from a certain Spanish forum, for designing the program icon.
- Buffer size changed from 32 KiB to 64 KiB.
You can grab the the latest build here and any feedback would be appreciated to DarkMatterCore.
Team Hackinformer signing out