With everyone so curious about the Nintendo Switch, we have already seen a few tricks pop out like DNSwitch to get into the portal of the web browsers. Then qwertyoruiop used one his exploits on it and LiveOverflow also went to town with the old Webkit vulnerability that is well known on iOS 9.3 with help from others. LiveOverflow, went into great detail on how this all works and it was probably enough information to get others started, which you can find here.
Now ReSwitched has put out PegaSwitch an exploit toolkit for the Nintendo Switch to help out everyone interested in getting started faster. Now, these tools will not allow homebrew but it’s a starting point for those that are curious what could be done or what could you find. Here’s what it does in a nutshell.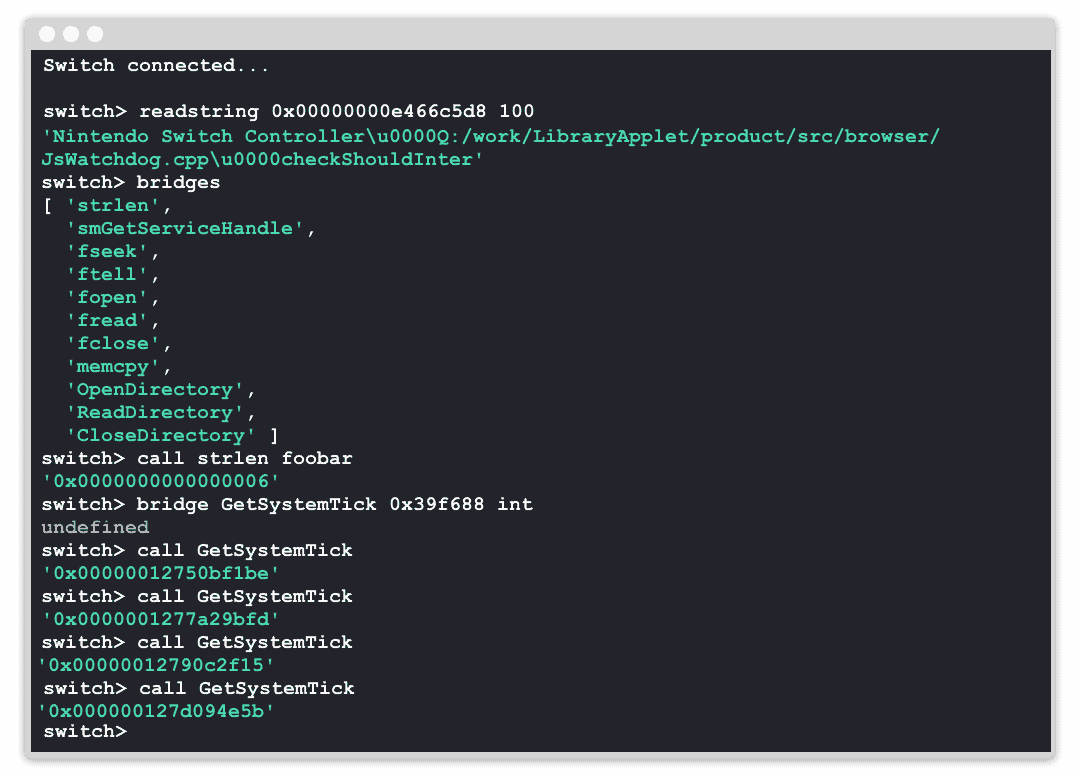
“By taking over WebKit, we are able to read/write memory, call native functions, and otherwise explore the functionality of the Switch from the domain of the WebKit process. This does not currently enable homebrew software, but is built to allow other hackers to work toward that goal.”
To set it up your going to need/do these things below.
- Install Node, Python 2.7, and Ruby
- Open ports UDP 53 and TCP 80 and 8081 on your firewall
- Run
npm install,pip2 install flask, gem install rubydns - Start the DNS server with sudo ruby rdns.rb $yourlocalIP (drop sudo for Windows)
- Start the web server with sudo python serve.py
- Start watchify with npm start
- Start the shell with node debug.js
- Point your Switch to the DNS server
- Go to the eShop or another area that will trigger the captive portal
- Watch the shell connect
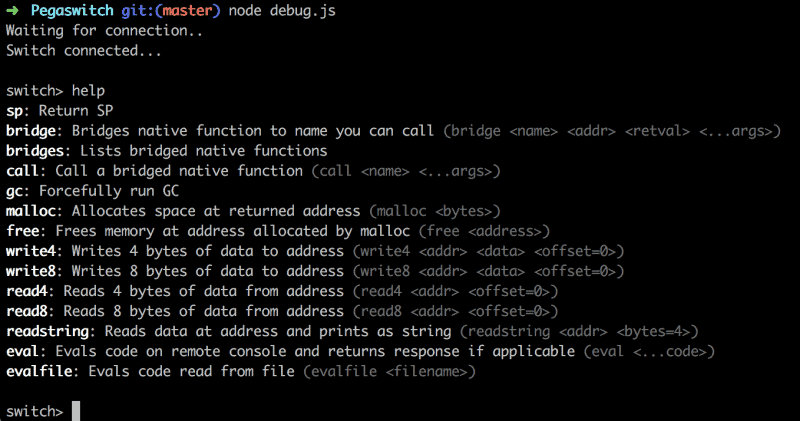
The shell is the default way to work with PegaSwitch is via the shell. Type help after the Switch connects to get a list of commands.
To get the rest of the info visit pegaswitch.com
Contributing to ReSwitched
To contribute to the project, join the Discord server with this link. More details about our Discord server, its channels, rules, etc. can be found here. If you’d like to contribute to the wiki as well, first register here then send your username to Daeken on Discord and request write access.
We are limiting write access on this wiki, as well as access to a secret chat room on this Discord server, to those with reverse-engineering experience or specific goals to learn. We want to allow everyone in, but we need to be able to keep certain details private to prevent bugs from being fixed too early, and things like that. Basically: If you know you want to help and have the skills (or at least the drive to get those skills) to do so, you won’t have a problem getting in.
For more info visit reswitched.tech